Nowadays smartphone has become a part of our life. From the very beginning of the day to our late night, our phone is our companion. I will not exaggerate but it is true that more than anyone else your phone is your best buddy.
Therefore, It is the duty of ours to defend our buddy from any damage. As you already know, smartphone users are divided into two parts:
1: iOS users
2: Android users.
Lets put the jokes, memes apart, both types have their own pros and cons and this is my personal opinion.

I am writing this article on demand, therefore we will discuss here iOS security. I assure you guys I will write on android also in my upcoming articles. So let's begin,
Former FBI computer scientist Randy pargmen says this about i-phone security.
"iPhone owners tend to feel more confident in the security of their phones than Android owners, and for good reason's true that iPhones and the whole Apple ecosystem keep customers safer from malicious apps, but that doesn't mean that all the data stored in the apps are safe from theft, Many apps store sensitive information on servers operated by the app developer or transfer the information unencrypted over the Internet. As soon as your information leaves your iPhone, it is outside of your control to protect it.,"
Therefore you should not ignore basic threats on iOS. Let's take a closer look at your i-phone security posture and let's see what are the precautionary measures one should take to protect your information.
1) Download Genuine Apps:
2) Updates
Do you wear bell-bottom pants? Do you wear an 80's polka dot scarf? if you are updated by fashion, your clothes, shoes, etc. You are updated with today's fashion right? Similarly your phone needs to be updated to avoid malware, bugs, misconfiguration that makes your phone under threat. Always enable "Automatic updates" in your setting.
3) Turn off weird permissions
Why your flashlight app needs to know your location? why your calculator want to access your camera? Limit your permission for all apps manually. Beware if an app is misbehaving after denying any permission which is not relevant to it.
By going to Settings > Privacy, you can view which apps have access to your contacts, calendar, photos, Bluetooth, microphone, camera, and health data.
4) Passcode
Dual security authentication is very useful to maintain the security of any phone. Along with the face recognition and fingerprint unlock facility passcode has its own importance. Something that you know and only you know about your phone will prevent you from unauthorized access
access Settings > Touch ID & Passcode (or Face ID & Passcode). Go to Change Passcode and tap Passcode Options to view the option for Custom Alphanumeric Code.
Never share your passcode to anyone.
5) Set login limitation
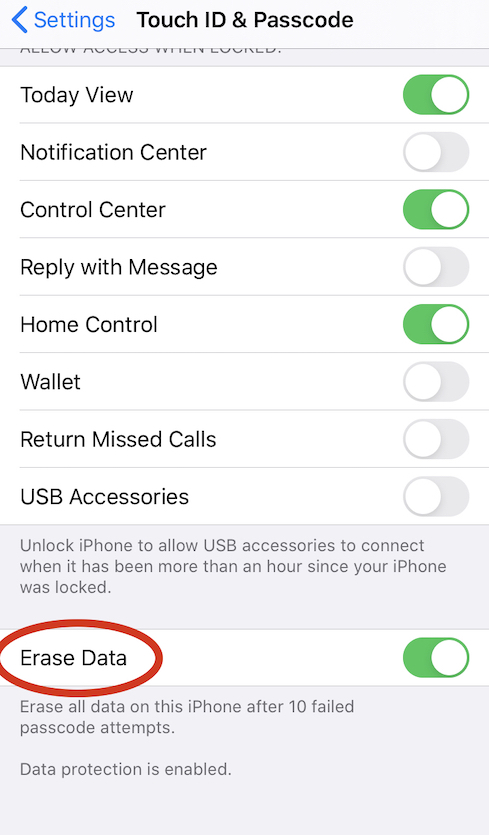
In case of the phone theft or loss you might be worried about your device falling in the wrong hands. there are also chance of brute-forcing for unauthorized access to your phone. To prevent this, you can set your "erase data" option. This automatically deletes all data on your phone after 10 consecutive incorrect login attempts. Access Settings > Touch ID & Passcode and scroll to the bottom to toggle Erase Data to the On position.
6) Safari security
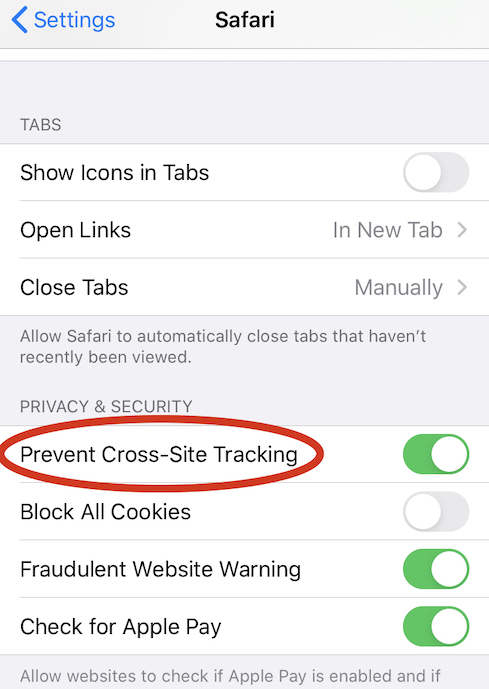
By not going to much technical for general readers, you can protect your self from the website which collects your data from your browser.
you can change the search engine from google to "duck duck go" if you have privacy issues. you can opt-out interest-based advertising.
7) Public Wifi access
It is not sure that all public wifi connections are genuine or safe to use. Cybercriminals will often use to broadcast their device as a public access point to intercept the data between you and your belongings. Always disable wifi and BlueTooth unless its known and genuine. Use a VPN connection to encrypt your activity.
So, These were the basic To-Do's to protect your i-phone from unauthorized access, data theft, etc.
Share your feedback in comments.
Stay safe...Stay aware.
Comments
Post a Comment